How to Choose a Security System
What distinguishes a professional security system from a cheap alarm system? Once you've decided you want to protect your apartment, house, or office, you face a choice: use a professional system or trust a cheaper alarm system with no certifications whatsoever. At first glance, both...

What distinguishes a professional security system from a cheap alarm system?

Once you've decided you want to protect your apartment, house, or office, you'll face a choice: use a professional system or trust a cheaper alarm system with no certifications whatsoever. On the surface, there seems to be a big difference between the two, and either device could help protect your home.
But a small, insignificant saving can lead to a lot of trouble. Cheap sensors often give false alarms and sometimes fail to alert you when real danger occurs. The device may suddenly malfunction, but the system won't notify you of the problem. The connection range is only just enough to cover the area to be protected, and sometimes even loses connection. The control application doesn't work as perfectly as it should. Your property, and even the lives of you and your loved ones, are completely left unattended when faced with an intruder. Furthermore, these companies don't agree to integrate their systems into the monitoring network, leaving you to handle the situation yourself when an alarm occurs.
To help you make the right choice, we've outlined six criteria for a reliable security system. Furthermore, we'll demonstrate exactly how Ajax perfectly meets these criteria.
1. The security system must have multiple connection methods.

The security system must be able to utilize multiple communication channels to transmit alarm signals to users and security companies: GSM, Internet, and Wifi.
Alarm systems with only one communication channel are unreliable. In the future, the connection between the devices could be lost due to environmental changes, preventing the delivery of alarm information to users or security companies. For example, this could happen if the SIM card runs out of credit or the network cable is cut. Furthermore, these systems can be easily sabotaged: by jamming the GSM signal (if only using a SIM card connection) or cutting the network cable (if only using a wired internet connection).
However, if the security system has multiple communication channels, one of which is used as the primary channel and the others as backups, such a system is far more reliable. In the event of a connection loss, the system can still function normally. The more communication channels there are, the greater the system's ability to provide timely alerts to users or security service organizations.
Communication channels must take different forms. If a system is equipped with multiple GSM modules without any other connection method, you effectively only have one communication channel. If the GSM frequency is jammed, the system will be completely isolated.
Another crucial issue is response time—how long it takes for the system to switch between two communication channels. With inexpensive alarm systems, this process can take tens of minutes. Meanwhile, a burglary typically only lasts 5-10 minutes.
So what communication channels does Ajax use?
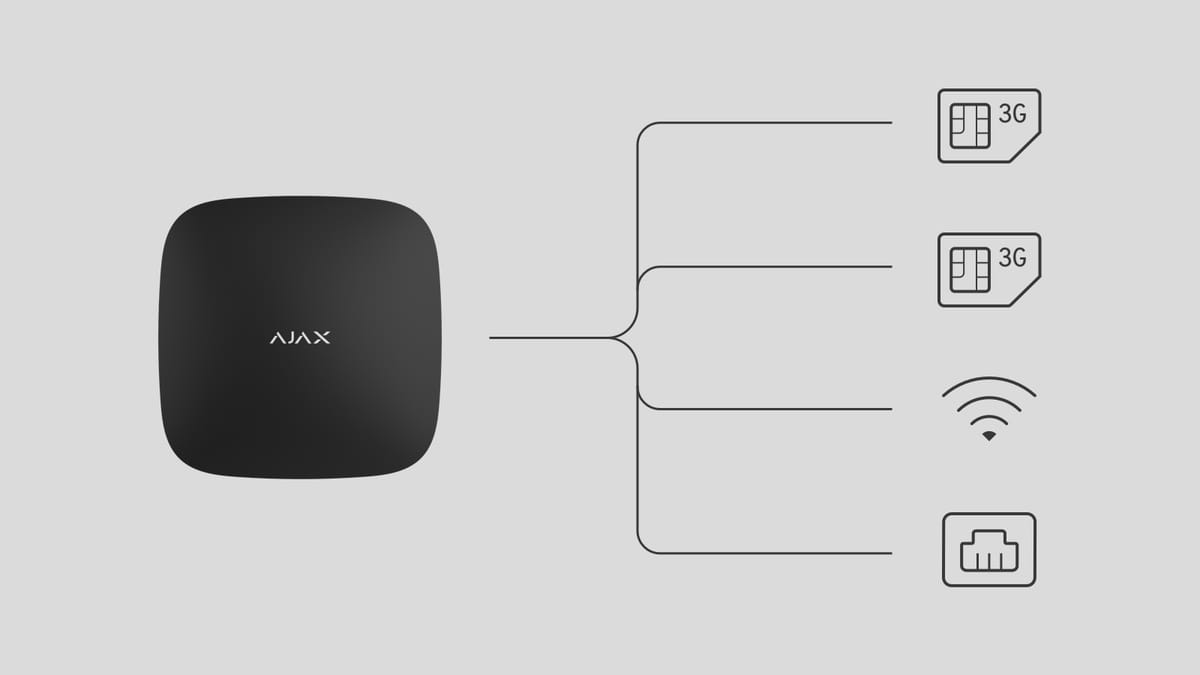
The hub uses GSM and Internet connections to transmit signals, and the Hub Plus is unique among system control centers as it utilizes four interconnected channels simultaneously: Wi-Fi, Ethernet, and two 2G/3G SIM card slots.
Switching from an internet connection (or Wi-Fi for the Hub Plus) to a SIM connection is completed in an instant. And switching between the two SIM slots of the Hub Plus will be completed within 4 minutes.
2. The security system must utilize a cloud storage facility.

As a rule, cloud servers represent the link between the control panel and the security system management application. They allow users to control all device functions via an internet connection, even from thousands of kilometers away. Additionally, the server sends notifications to mobile phones about system events or alerts.
For a professional system, the Cloud server also monitors connections to security devices and their operational status through dashboard scans. The higher the scan frequency, the faster the server can identify problems and alert users or security companies about the situation.
How does the Ajax security system utilize the Ajax Cloud service?
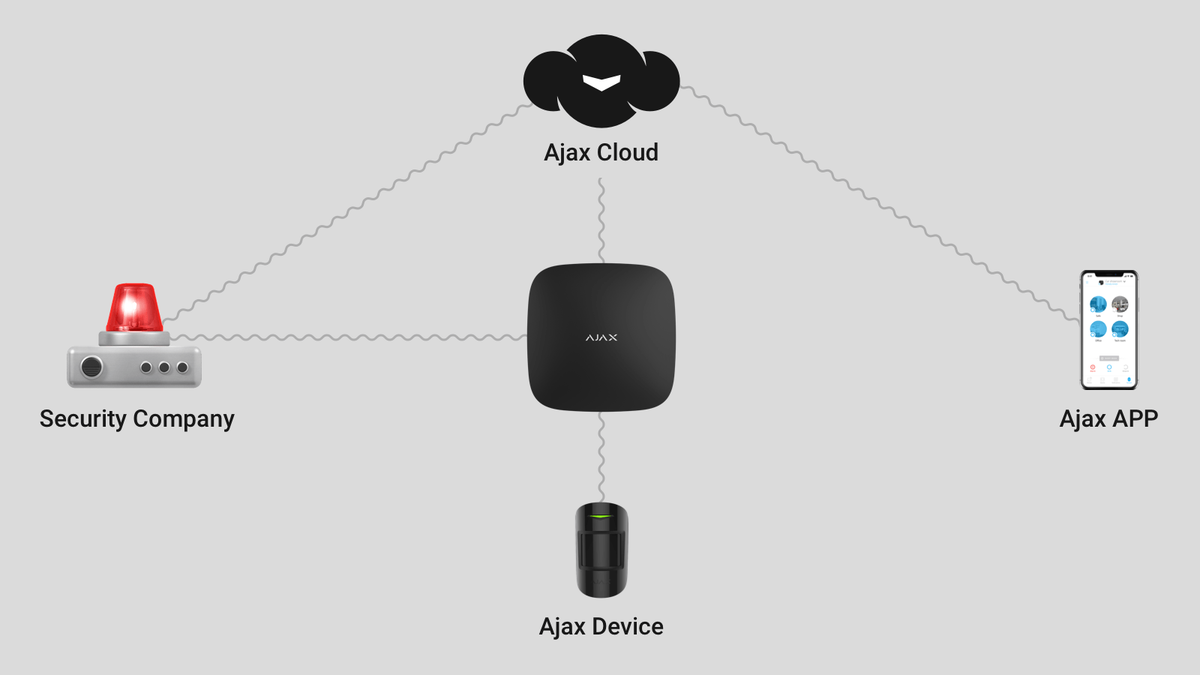
In addition to controlling hubs via the app and receiving notifications on your phone, the Ajax Cloud service also displays the status of the security system. The service will regularly (every 10 to 300 seconds, depending on the settings) communicate with the hub and update the status of the devices in the Ajax application.
If the Hub is disconnected, the Ajax Cloud service will send alerts to users and security companies.
👉🏻 How long does it take to send a signal loss notification to the Hub?
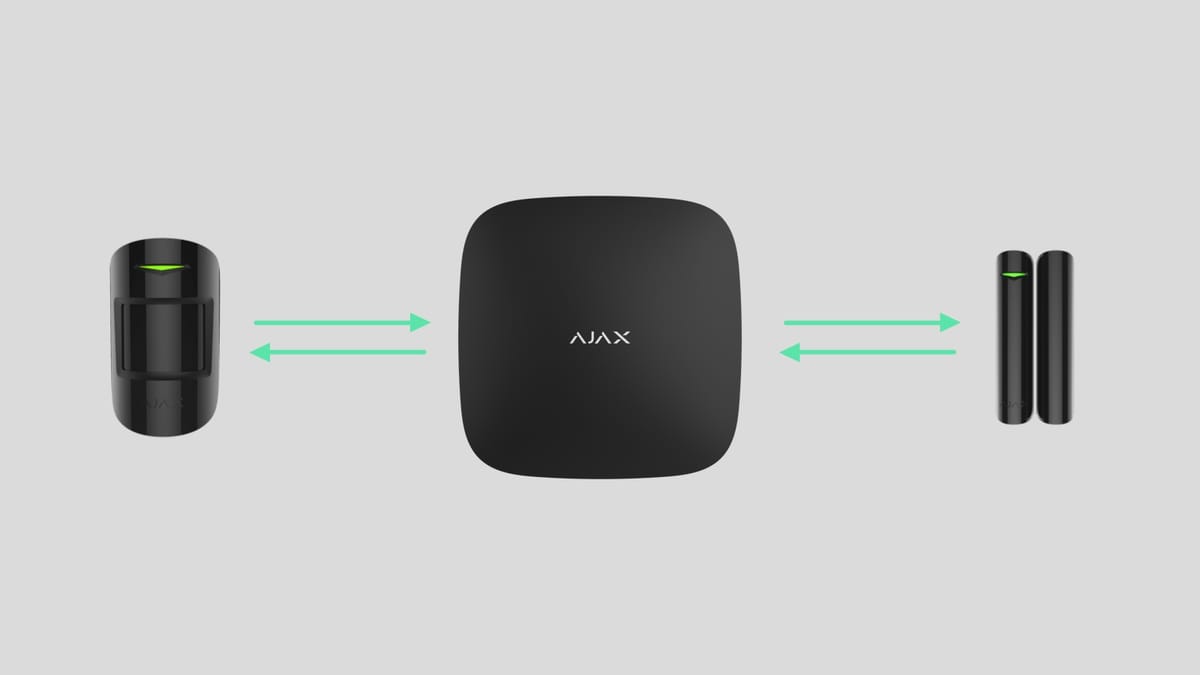
3. Security devices must use reliable connectivity technology to communicate with the control panel.
For wireless security systems, information exchange between the control panel and the sensors is via radio waves. Communication must be extremely reliable; even temporary loss of connection is undesirable (it leads to increased alarm triggering time), and complete loss of connection is unacceptable (resulting in the user and security company being unaware of an ongoing alarm).
As a rule, professional systems must operate at 433MHz or 868MHz and use a frequency band rather than a fixed frequency for communication between the control panel and sensors. This allows the system to automatically switch frequencies in the event of a malfunction or vandalism. This technology is known as "frequency hopping".
|
Why is Wi-Fi unsuitable for communication between security devices?
|
What type of wave technology does Ajax use?
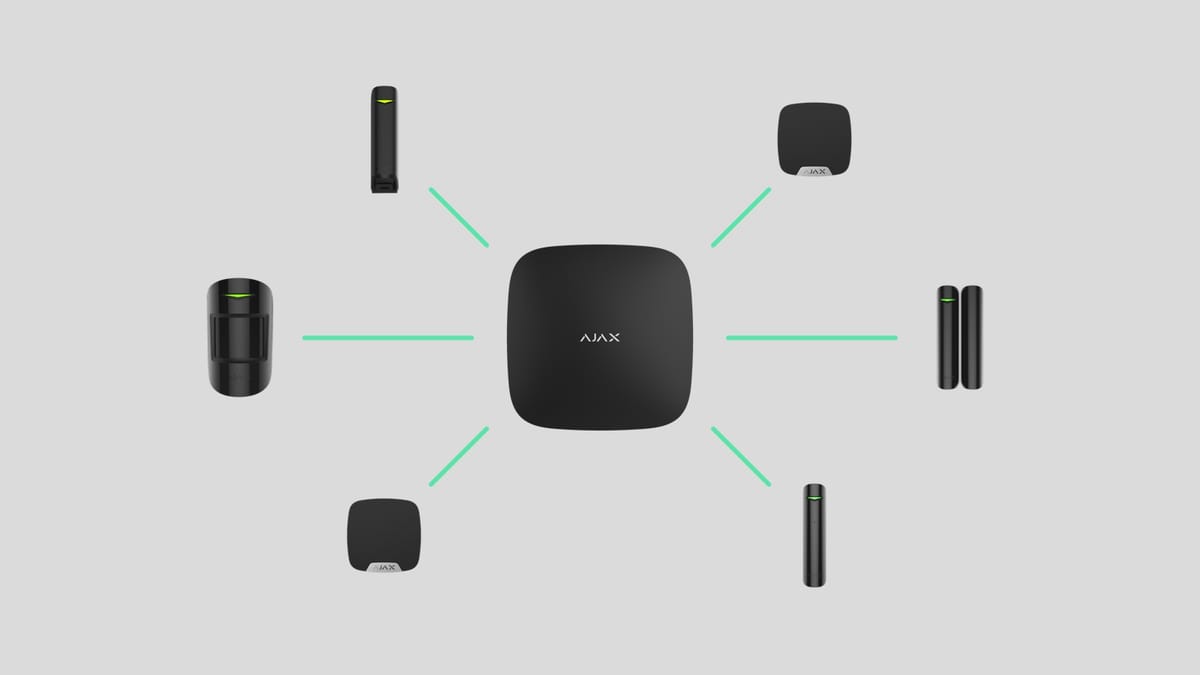
To communicate between the Hub and devices, the Ajax security system uses Jewellery wave technology. Its operating range is from 868.0 to 868.6 MHz or 868.7 to 869.2 MHz (depending on the area) and it continuously monitors interference levels in the communication channel. As soon as interference levels exceed the permissible value, the Hub detects signal interference and immediately switches to a less interfered-with frequency. An alert is then sent to the user and security companies regarding the incident.
Jeweller transmits alerts in less than 0.15 seconds, automatically adjusting signal strength to minimize device battery consumption and ensuring a connection range of up to 2000 meters.
4. Communication between devices in the security system must be two-way (duplex).
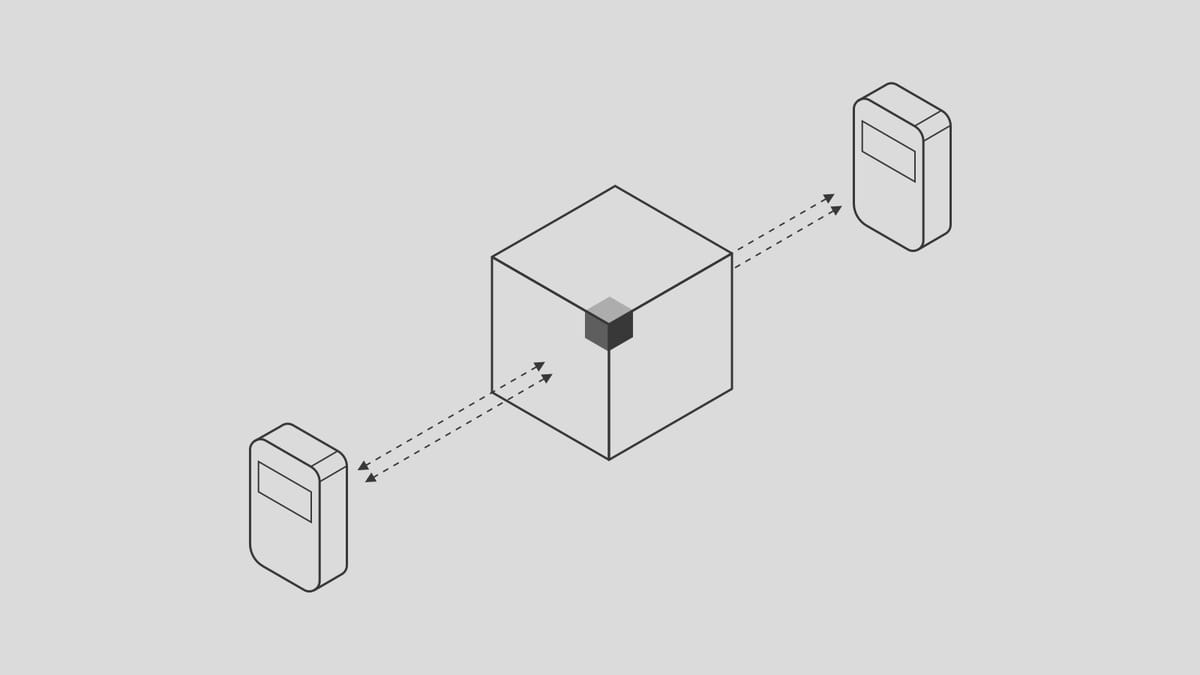
Communication between devices in a security system can be one-way or two-way. In the first case, the sensors send alarm signals and reports of incidents to the control panel, but the control panel does not communicate with those devices. If a device malfunctions (due to vandalism or product defect) or the connection is interrupted, the control panel will not be aware of the situation. Neither the user nor the security company will receive notification of a breach in the security system.
In security systems with two-way communication, the control panel and sensors exchange information. The sensors continuously send alerts until the control panel acknowledges receipt. In this case, there is no risk of data loss from short-term disconnections. The reliability of these systems is many times greater than the previous type.
How does the Ajax security system utilize two-way communication?
The sensors will send status reports to the Hub every 12 seconds or so. The Hub will respond to the sensor notifications and update device information on the app. If a device is unresponsive for any reason, the Hub will consider the device lost and notify the user and security company of the situation.
When sending an alarm, the detector requests confirmation from the control center. If the detector does not receive a response, it will continue communicating the alarm until the control center accepts and processes the alarm signal.
Two-way connectivity allows users to remotely monitor devices and change their settings via Ajax applications: sensor sensitivity, alarm siren volume and their response to alarms, which security groups they belong to, etc.
👉🏻 How long does it take for the hub to detect a loss of connection with the sensor device?
5. The security system encrypts data and is protected against tampering.

Data transmission between sensor devices and the control panel must be encrypted and protected against tampering. The underlying issue is preventing device overwriting, including, in the worst-case scenario, overwriting the remote user's control settings, allowing an intruder to gain full control of the system.
The optimal solution is to encrypt the radio signal with a complex algorithm, because the older the algorithm, the easier it is to hack and gain administrative control of the system. For example, cracking data encrypted by 128-bit AES encryption would take thousands of years, while an alarm system with outdated encryption can be hacked in just minutes using a "code grabber".
👆🏻 A code grabber is a device used to interfere with the signals between a security system and a control device (remote or keypad) in order to hack into the system.
How is Ajax protected from counterfeiting?

Instead of using basic algorithms and solutions, Ajax uses a solution they developed themselves. All data sent is encrypted with the AES algorithm and a floating-point key. Each Ajax device has a unique identifier, and the Jeweller wave protocol provides a system of priorities and markings to identify each device. The security system cannot be disabled by a remote key not linked to the system.
Ajax's reliability is confirmed by EN 50131 certification, and the system's security devices are rated level 2 integrity, meaning they are ready to face even the most experienced attackers.
👉 What is that level and why is it so important that a security system must have it?
6. The security system is connected to the monitoring centers of a security company.

The job of a security system is to identify danger as early as possible. But simply recognizing the problem isn't enough – you need to react to it correctly. Upon receiving an alarm, one might contact the police (confronting the criminal oneself is unwise). However, a wiser course of action is to trust the professional response by connecting your security system to the monitoring centers of security companies.
Security organizations only connect certified security systems to their monitoring systems. During the certification process, security equipment is tested by licensed independent laboratories to: check functionality, weather resistance, mechanical interference, magnetic fields, connection quality, and the impact of external factors on the equipment. If you fail even one test item, you will not receive the certification.
Before a new device is put into practical use, security companies will install it inside a test facility (apartment, house, office, etc.) along with certified security systems. If the new system can achieve the same level of reliability and accurately identify threats as the old system, then it will be connected to the central monitoring station.
How to connect Ajax to monitoring centers?
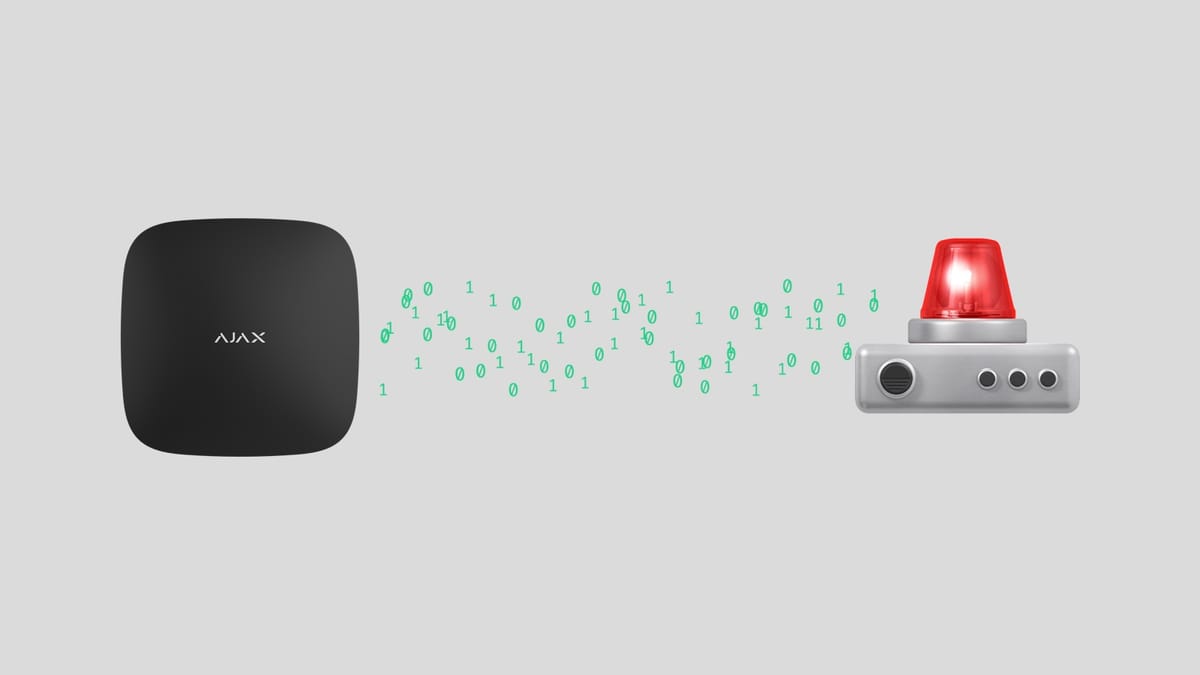
The Ajax security system can be connected to monitoring centers of security organizations in almost anywhere in the world. You can select a security company directly within the app:
-
Go to the Security companies section in the hub settings (Devices → Hub → Settings ⚙️ → Security companies)
-
Select a security company from the list and click Send Monitoring Request.
Only a reliable, professional security system that provides comprehensive protection and ensures your awareness of the situation at the premises can be entrusted with the protection of people and property.
-
The security system remains connected thanks to multiple communication channels.
-
Users and security companies are always aware of the security system's operational status thanks to the cloud server continuously exchanging information with devices located on the protected premises.
-
Sensors, control devices, and alarms are always connected to the central unit (control panel) when the security system uses the correct type of communication technology.
-
In the event of a malfunction or vandalism, the control panel will be notified of the problem, and you and the security company will be alerted to the situation.
-
An intruder will be unable to gain access to your security system and will not be able to deactivate or weaken the protection system because the possibility of hacking and spoofing has been completely eliminated.
-
When an accident occurs, the security company will send a rapid response team to the scene within minutes.